NTLM Hash Generator
Use our fast and reliable NTLM hash generator online tool to generate high-quality secured unique NTLM hashes and protect your sensitive data from unauthorized access.
If you use this great tool then please comment and/or like this page.
Average Rating: Tool Views: 677
Average Rating: Tool Views: 677
Subscribe for Latest Tools
How to use this NTLM Hash Generator Tool?
How to use Yttags's NTLM Hash Generator?
- Step 1: Select the Tool
- Step 2: Enter The Text And Click On The Generate NTLM Hash Button
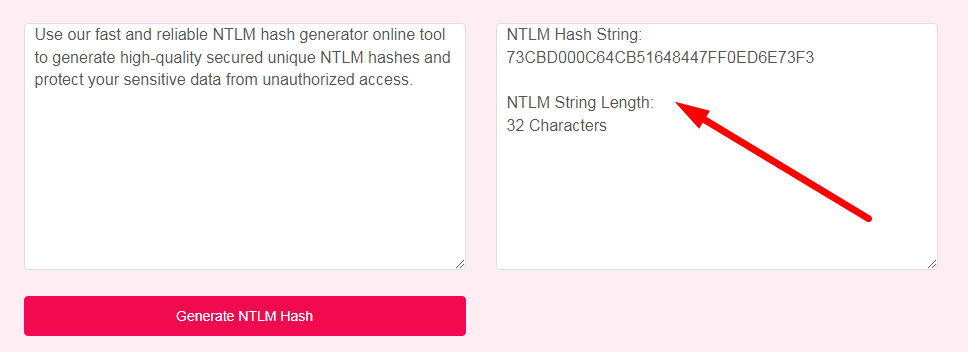
- Step 3: Check Your NTLM Hash Generator Result
If you want to link to Ntlm Hash Generator page, please use the codes provided below!
FAQs for NTLM Hash Generator
What is a NTLM Hash Generator?
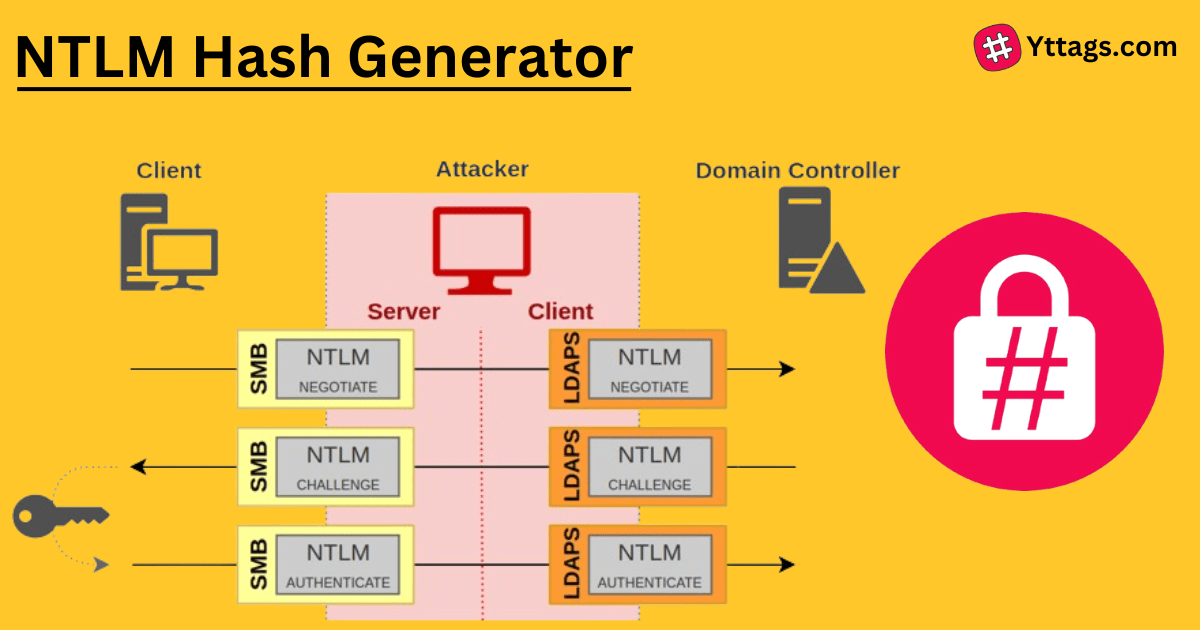
An NTLM Hash Generator is a tool that creates NTLM (NT LAN Manager) hash values, commonly used for password hashing in Windows-based authentication systems. NTLM hashes are employed for security and compatibility in network authentication protocols.
How are NTLM hashes generated?
The NTLM hash is encoded by taking the user's password and converting it into a 16-byte key using an MD4 hash function. This key is divided into two halves of 8 bytes each, which are used as input to three rounds of DES encryption to generate a 16-byte output that represents the NTLM hash.
What is the bit size of NTLM hash?
Both hash values are 16 bytes (128 bits) each. The NTLM protocol also uses one of two one-way functions, depending on the NTLM version; NT LanMan and NTLM version 1 use the DES-based LanMan one-way function (LMOWF), while NTLMv2 uses the NT MD4 based one-way function (NTOWF).
How many characters is an NTLM hash?
As NTLM hashes are uppercase 32 hex digits in length, you can use this program to generate random 32 character long hashes.
What is NTLM used for?
Windows New Technology LAN Manager (NTLM) is a suite of security protocols offered by Microsoft to authenticate users' identity and protect the integrity and confidentiality of their activity.